Proxy integration is a critical component of modern IT architecture, especially for organizations looking to enhance privacy, scale infrastructure, and improve performance. By effectively integrating proxies into your systems, you can shield sensitive data, manage traffic intelligently, and optimize access across global networks.
In this guide, we’ll explore 7 essential tips to implement proxy integration smoothly — from selecting the right type of proxy to handling authentication, logging, and performance tuning.
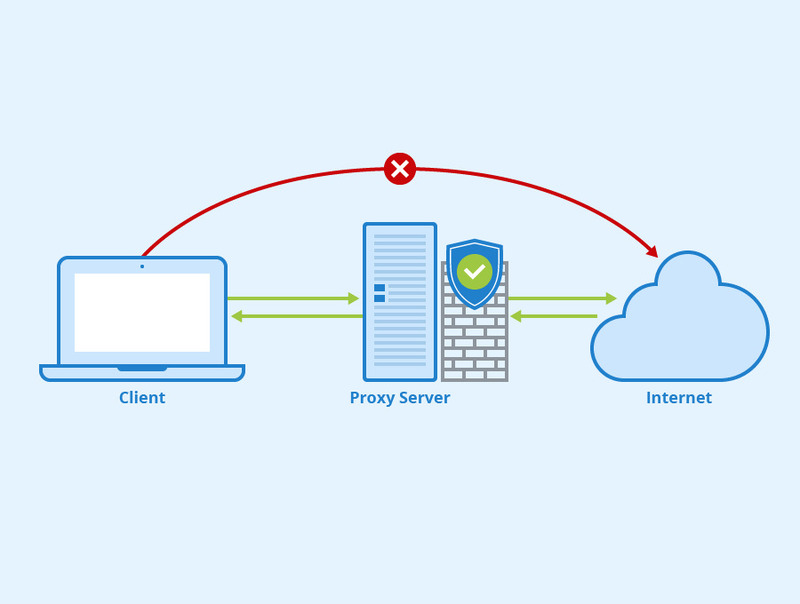
1. Understand the Role of Proxy Integration in Modern Infrastructure
Before you implement proxies, you need to know what they do. A proxy server acts as an intermediary between a client and the internet, allowing you to filter traffic, enforce security rules, and anonymize requests.
When properly deployed, proxy integration provides:
-
Enhanced security through IP masking and request filtering
-
Load balancing and traffic routing
-
Access control and usage monitoring
-
Bypass of geo-restrictions and content filtering
2. Choose the Right Type of Proxy for Your Use Case
There are many kinds of proxies, and your use case will determine which to choose:
| Type | Best For | Pros | Cons |
|---|---|---|---|
| HTTP Proxy | Web content filtering, caching | Easy to implement | Not encrypted |
| HTTPS Proxy | Secure communication | SSL encryption | Slightly higher latency |
| SOCKS5 Proxy | Gaming, streaming, P2P | Versatile protocol support | More complex to configure |
| Residential Proxy | Web scraping, ad verification | Harder to detect, real IPs | More expensive |
| Datacenter Proxy | Bulk traffic, automation | Fast and stable | Easier to block |
| Mobile Proxy | Social media, mobile network testing | Real mobile IPs, high trust rate | Slower speeds |
Make sure your proxy integration matches your tech and business requirements.
3. Use a Centralized Proxy Management System
Managing multiple proxies manually is error-prone. Instead, adopt a proxy management platform or integrate with a programmable API to:
-
Rotate proxies automatically
-
Monitor uptime and latency
-
Switch between proxy pools based on load or geography
-
Enforce dynamic authentication policies
Popular tools include:
-
Bright Data Proxy Manager
-
ProxyMesh API Gateway
-
Smartproxy Dashboard
Centralizing your proxy integration helps with visibility, scalability, and auditing.
4. Optimize Authentication and Access Control
A major concern in proxy integration is security — especially if proxies are handling sensitive or internal data.
Best practices:
-
Use token-based or encrypted authentication (OAuth, TLS)
-
Apply user-role permissions at the proxy layer
-
Avoid storing credentials in plain text
-
Log all access attempts and policy violations
Implement IP whitelisting and session limits to prevent abuse and overuse of proxy services.
5. Monitor and Log Proxy Traffic
Monitoring is a crucial component of a successful proxy integration. You should track:
-
Request origin and destination
-
Response times and error rates
-
User behavior and request frequency
-
Bandwidth usage
Use tools like ELK Stack (Elasticsearch, Logstash, Kibana), Grafana, or Prometheus to analyze and visualize this data in real time.
Logging also helps detect:
-
Unauthorized access
-
DDoS attempts
-
Proxy abuse
-
API scraping
6. Plan for Failover and Redundancy
Proxy downtime can cripple critical systems. To prevent this, ensure your proxy infrastructure is built for high availability:
-
Use redundant proxy servers (active-active or active-passive setup)
-
Implement health checks and automatic failover
-
Distribute proxy load across multiple data centers or regions
-
Store configuration backups and rotate IPs dynamically
A reliable proxy integration strategy anticipates and recovers from failure without service disruption.
7. Evaluate Performance and Fine-Tune Regularly
After integration, keep measuring proxy performance with benchmarks:
| Metric | Target |
|---|---|
| Average latency | < 200ms |
| Connection success rate | > 98% |
| Request throughput | Consistent under load |
| Error rate | < 1% |
Conduct A/B testing to compare proxy configurations. Track DNS resolution times, SSL handshakes, and keep-alive settings. You may need to adjust:
-
Timeout settings
-
Retry limits
-
Connection pooling logic
Successful proxy integration is not a “set it and forget it” task — it’s a continuous optimization cycle.
Final Thoughts: Make Proxy Integration a Core Part of Your Infrastructure Strategy
As your digital infrastructure grows, proxy integration will no longer be optional — it will be essential. Whether you’re protecting backend APIs, managing user access by region, or building a resilient scraping system, using proxies effectively gives your systems an edge in security, scalability, and performance.
By following these 7 best practices, your organization can integrate proxies seamlessly and unlock their full potential.
